Advanced Cybersecurity Agreement
Security Hardening Isn’t TOUGH
Thanks for meeting with us!
Often times organizations have defined the cybersecurity problem as too complex, too technical and too expensive.
Our charter is to help organizations identify gaps, close them and mitigate their cybersecurity affordably.
Our mission is to be a world class cybersecurity relationship provider.

What is SUCCESS from the “Cybersecurity Department?”

IDENTIFY / CLOSE / MITIGATE GAPS

RECOVER

BUSINESS & BUDGET ALIGNMENT

PROOF
Cyber FITNESS
Organizations must dismiss the notion that cybersecurity is a one and done exercise. Cybersecurity is an ongoing regimen that gets you fit and keeps you fit. Organizations can’t backup their data once, patch their systems once, scan their systems once, audit their systems once. Use the framework, get the right equipment, exercise regularly.
Let’s Talk STRATEGY
What are the Four B’S of Cybersecurity?
Be Informed
Latest
Keep up to date but not in the weeds
Decision Making
Right decisions at the right levels. Trust others.
Strategy
Where are we?
Where are we headed?
How will we get there?
Realistic
Shit happens. How bad depends on the maturity of your controls.
Be Practical
Bite Sized Meals
Don’t try and eat the elephant all at once.
Team Sport
Establish the right roles and players. Only as a team will you succeed.
Prevention versus Cure
Seatbelt versus 6-million-dollar man.
Be Boring
Framework
vCISO
Choose an industry framework as your guiding light. Not an interesting opinion or a shiny new widget.
Cybersecurity needs a champion driving results, progress and alignment. Success has to be managed.
Policy
Clear, concise, easy to understand.
Legal and compliant with 3rd party standards. (insurance, regulatory bodies, frameworks)
Tools
Clear policy that defines proper use.
Install, configure, update, monitor, and leverage.
Be Prepared
Have controls
Have a plan
Test
What are the key functions of successful
“CYBER RISK MANAGEMENT?”
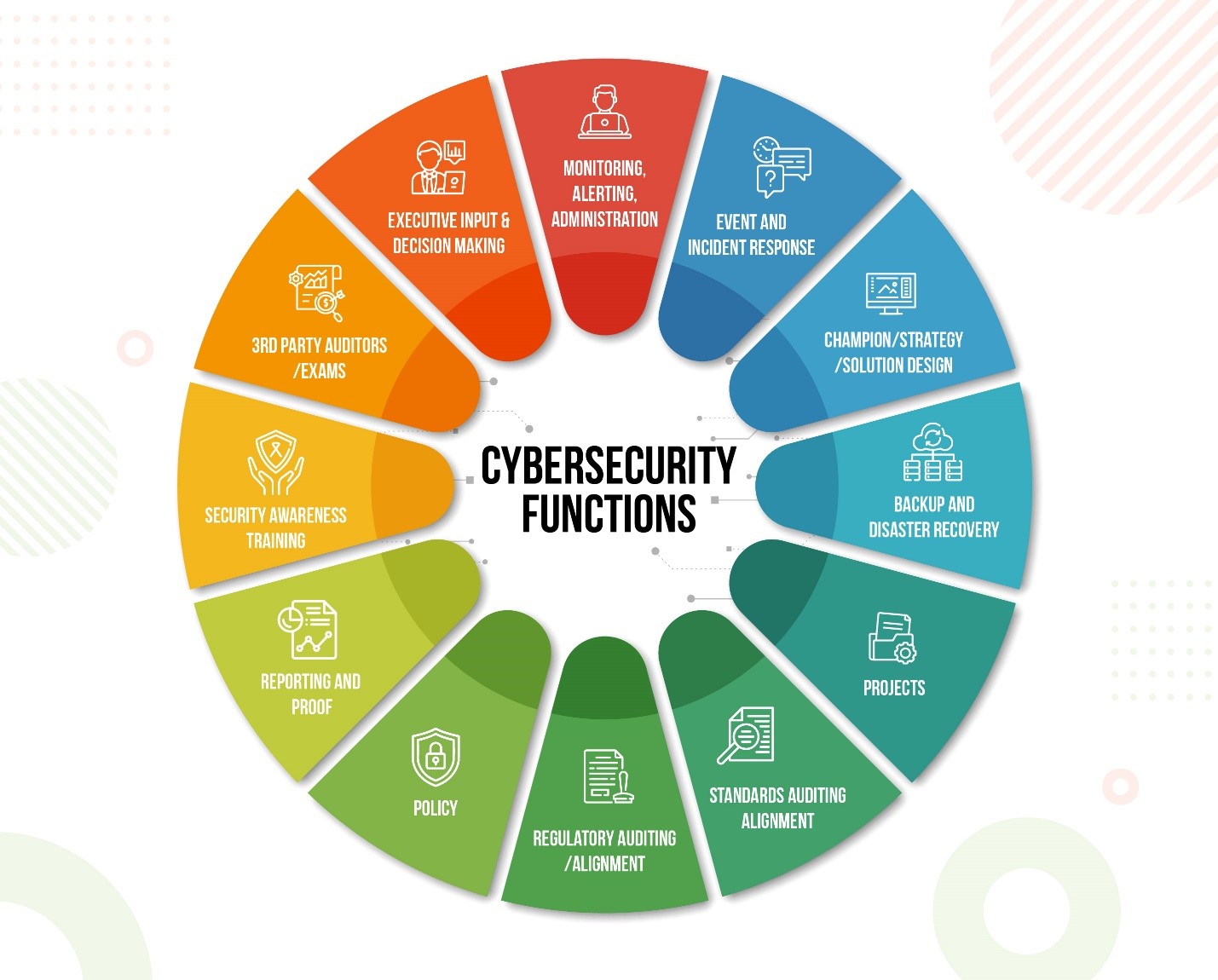
What is included within an Advanced Security Agreement?
MANAGED SECURITY – HARDWARE, SOFTWARE AND SERVICES
Endpoint (PC’s, Servers and Mac’s) Detection and Response (EDR)
Deploy EDR
Configuration of EDR
Monitoring of EDR
Security Information and Event Management (SIEM) / Security Operations Center (SOC) / Managed Detection and Response (MDR)
Configuration of devices for SIEM log storage.
Automatic collection of logs from devices configured to use the SIEM.
See quote for log retention duration details.
Desktop Application Patch Management
Automatic updating of desktop applications supported by Desktop Application Patch Management software.
Remote Monitoring & Alerting (8x5 or 24x7)
Monitoring of security events for devices connected to the SIEM.
Response to generated alerts based on severity.
Alerting in accordance with customer provided incident response plan.
SOC Response Desk
Remote resolution of events during First Call's operating hours either on a T&M or Fixed Price basis. The billing approach is dependent on other IT Services agreements with First Call.
Support for reporting as required for compliance or regulatory needs
3rd Party IT Audit Participation
Virtual Chief Information Security Officer (vCISO) audit participation.
vCISO review and recommendations upon audit conclusion.
*Up to 4 audits per year
virtual Chief Information Security Officer (vCISO)
Cybersecurity Steering Meetings
Onboarding
Other advice, budgeting, solution quotes
Completion of vendor due diligence package requests from 3rd parties for First Call or any of its vendors.
Security Alignment Manager (SAM)
Pre-scheduled SAM sessions
IT security standards auditing
Proactive alignment with standards
Risk reduction
Security steering input
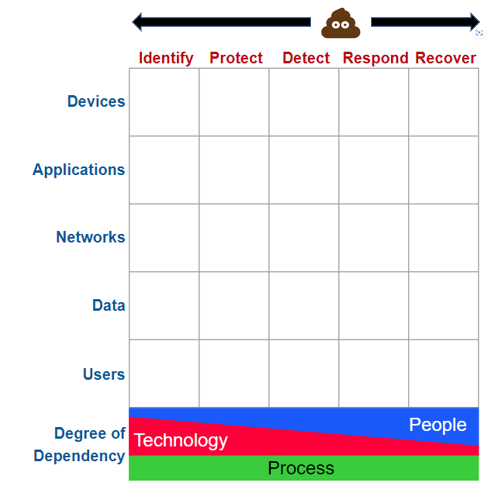
What Is A Security Alignment Manager (SAM)?
Think of a SAM like an auditor. They are regularly performing a review of your IT assets against cybersecurity standards. Finding the gaps, improving documentation, proactively reviewing the environment to reduce risk, improve standards alignment, documentation and proof for all involved.
This role involves understanding the organization’s devices, applications, networks, data, and users to ensure that the appropriate cybersecurity measures are in place to protect them.
Key Responsibilities of a Security Alignment Manager:
Conducting risk assessments to identify potential security risks and vulnerabilities
Monitoring and reporting on the effectiveness of cybersecurity controls
Coordinating with internal teams to ensure that cybersecurity requirements are met.
Collaborating with external partners to ensure that security requirements are met.
First Call’s SAM plays a critical role in ensuring that an organization’s cybersecurity program is aligned with its overall business strategy and is designed to protect its critical assets from cyber threats
What Is A vCISO ?
First Call’s Virtual Chief Information Security Officer’s are our senior executives responsible for managing the overall security of our client’s information systems and data. Their primary role is to ensure that the organization’s information and data are protected from cyber threats.
Key Responsibilities of a vCISO:
Developing and implementing an overall cybersecurity strategy and roadmap for the organization.
Overseeing the development and implementation of cybersecurity policies, procedures, and guidelines.
Identifying and mitigating security risks and vulnerabilities in the organization’s information systems and networks
Managing the organization’s response to cybersecurity incidents and breaches
Overseeing the selection and implementation of cybersecurity technologies, such as firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) systems
Ensuring that employees are trained on cybersecurity best practices and are aware of their responsibilities in maintaining the security of the organization’s information and date
Collaborating with other stakeholders, such as the owners or executives to ensure that cybersecurity is integrated into the organization's overall strategy.
Our vCISO’s play a critical role in ensuring the confidentiality, integrity and availability of an organization’s information and data. As cyber threats continue to evolve and become more sophisticated, the role of the vCISO becomes increasingly important in protecting an organization’s critical assets from cyber attacks
How Do The FEES Work?
Onboarding
First Call charges an onboarding fee that is based on the monthly recurring agreement. This is charged upfront and must be paid before work begins.
Recurring
The agreement is billed monthly at the beginning of the month. Credit card, e-check or ACH payment is required.
What are the basic terms of the agreement?
36-month contract
Choosing A Cyber SECURITY Partner
We hope the time spent and information provided has been helpful so far. We want a successful long-term relationship, not to be a faceless remote Cybersecurity vendor. Please provide us feedback on how else we can make the journey of finding a good fit better. We understand that choosing the right cybersecurity partner can be a crucial decision for your organization. It involves entrusting a third-party with protecting your sensitive information and critical assets from cyber threats.
Here are some factors to consider when choosing a cybersecurity partner:
Expertise and Experience: Look for a partner with expertise and experience in your industry and with the specific cybersecurity solution that your organization needs.
Range of Services: Consider the range of services offered by the partner, and ensure they are aligned with your organization's cybersecurity needs. Look for a partner that offers a comprehensive suite of cybersecurity services, including risk assessments, incident response, threat monitoring and compliance management.
Reputation and References: Conduct thorough research on your partner’s reputation in the market and seek references from their existing clients.
Approach and methodology: Understand you partner’s approach towards delivering cybersecurity services and ensure that their approach is aligned with your organization’s risk management strategy, compliance requirements and security goals
Flexibility and Scalability: Look for a partner that can provide flexible and scalable solutions that can adapt to your changing needs. Assess whether they can they grow with your business.
Cost-effectiveness: Finally, consider the cost of the partner’s services and ensure that they provide value for money.
Some Of Our Happy CUSTOMERS



ARE WE THE IT PARTNER YOU ARE LOOKING FOR?
Schedule a time to have us evaluate your current IT frustrations and show you how our Better Way can solve them.
CONTACT FIRST CALL
CHOOSE THE BETTER WAY
GET CONNECTED
NEED SUPPORT?
FOR SALES
Sales@firstsolution.com | 406.721.6462
HelpDesk@firstsolution.com | 406.540.1969
FOR WEB SERVICES
WebHelp@firstsolution.com | 406.540.1969







